You know you need to make your products as secure as possible – but have left yourself exposed with weak license key encryption?
In my previous blog I covered software security concepts and software licensing security which I’ll continue with here, including the encryption of software license keys.
Software Licensing and Cryptography
 The “authenticity” principle in CIA mentioned in the first blog is important when producers consider the encryption of their software license keys via cryptography[1] – the process by which information is encrypted so that it’s meaning is hidden from those who don’t know how to unlock or “decrypt” the information.
The “authenticity” principle in CIA mentioned in the first blog is important when producers consider the encryption of their software license keys via cryptography[1] – the process by which information is encrypted so that it’s meaning is hidden from those who don’t know how to unlock or “decrypt” the information.
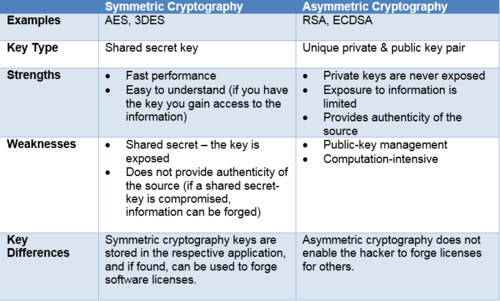
While there are several types of cryptography I’ll focus on two of the most commonly used in software license key encryption: symmetric and asymmetric cryptography.
Symmetric cryptography uses a shared “secret key” or set of keys to encrypt data. The secret key(s) must be shared between the parties that will use them prior to data disclosure.
The weakness of symmetric cryptography is that the secret key(s) used to generate licenses must be shared amongst all software in the code base. Unfortunately this means that hackers could crack the shared secret key(s) and then forge licenses for all software that uses the shared secret key(s). There are multiple key generators on the internet for various applications that allow anyone to forge licenses that would enable all capabilities of the software.
Asymmetric cryptography or “public-key cryptography” is generally a more secure type of cryptography since it uses a pair of keys known as a “public/private key” pair. Asymmetric cryptography is used to encrypt most secure (e.g. financial) transactions that are transmitted over the internet.
The idea is simple: Only the customer/end user writing the software should have access to the private key, while the public key is embedded in all software components that are used to verify the authenticity of the licenses (that can only be generated using the private key). From a software licensing perspective, producers generate their own private and public key pairs, which means that if one producer’s private key is compromised, other products can’t be accessed via forged licenses.
To help illustrate the key differences I’ve include the table below that depicts some of the key differences between symmetric and asymmetric cryptography types as they relate to software license key generation:
The reality is that any license key generator can probably be hacked given enough time and effort, and that the implementation itself will have a lot to do with the level of security. The cryptography technology alone will not guarantee security – producers need to be diligent about their licensing key generation processes and technology, and they need to be implemented properly.