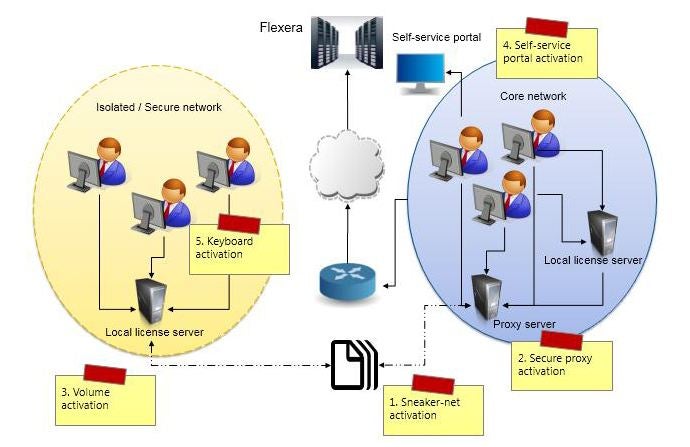
Today many software applications require an end user to go through a software licensing activation process. The ultimate goal of an activation process is to reduce or minimize software piracy, in other words, prevent the sharing of software between people in a way that infringes on the software’s end user license agreement (EULA). The activation process becomes much more challenging in a disconnected network environment (i.e. branch offices and/or high-security zones within a production or core network environment), since these disconnected network segments are air-gapped or separated by a firewall that limits or prevents communication to and from other network segments (see diagram).
If you are an application producer that requires support in such an environment, you should consider alternative options to product activation. Here are a few things to consider:
- Sneaker-net activation: the most common product activation method to support the disconnected network. This involves exchanging a file between the entitlement system and the end points. In the exchange, the end point would provide the machine fingerprint of the system and the entitlement system would generate the appropriate license for the specific system. The end user in this case would be responsible for transporting the file between the entitlement management system and the end point.
- Secure proxy activation: in most cases, the network administrator would have a secure proxy server that would allow a control connection to the Internet due to security policy to ensure data privacy. This process is similar to the normal activation process in the connected environment, with an additional step that the application must establish and be authenticated to the proxy server first.
- Volume activation and transfer: in some cases especially in large enterprise deployments, the ability to automate activation for hundreds and maybe thousands of applications can be overwhelming task for an administrator if the only option is through a sneaker-net approach. To overcome this, an alternative approach would be to leverage the local license server to automate the software license activation process. So, instead of the application calling home to the entitlement management system over the Internet, the application would exchange the activation information with the local license server to activate.
- Self-service portal: similar to sneaker-net activation, the most common way of activation in a disconnected environment is to allow the actual end user to self-activate his application. Usually, credential and activation keys are provided to the end user during the order process. The end user is given a set of instructions, usually about going to a web portal, entering in his activation key and downloading the license for his application.
- Keyboard only activation: in rare cases especially when dealing with any government entities, there is absolutely no digital exchange between the isolated network to the outside world. Most of the time, the only input device is through a keyboard. This model involves exchanging machine fingerprint information and activation keys over a non-digital media (e.g. paper), so that an end user in this secure environment is able to enter in the activation key in order to activate the software product.
Applications are everywhere, and product activation is one solution to combat against software piracy. With Revenera’s Software Licensing Solutions multiple disconnected and in-product activation scenarios are supported. The range of support spans from simple disconnected systems to highly, secure environments where no information about the environment is ever allowed to leave.
What types of product activation processes does your organization offer? What do your end-users prefer?