On September 14th, The White House published a memorandum addressing the state of the global software supply chain. In order to reduce the risk of cyber threats and the loss of sensitive information, the United States Government issued this statement which requires federal agencies to comply with NIST guidance when using third-party software.
The update comes just after the Strengthening American Cybersecurity Act of 2022 was passed in congress, which was a response to the May 2021 Executive Order on the nation’s cybersecurity.
This memo furthers the already rigorous array of new measures that the Biden administration has put into place over the past year. Modernizing their approach to secure software development, the Biden administration has released a range of memos around the best practices to secure the supply chain:
Modernizing their approach to secure software development, including:
In response to the mounting threats, these new guidelines implement a rigorous framework for modern cybersecurity protections across all systems.
What Does This Memo Include?
The NIST Guidance outlined in the memo provides additional recommendations to federal agencies, implementing an approach that minimizes risk and promotes secure software development.
Although the guidelines set out in the memo cover a range of topics, there are actually only two actions that are set in stone. All Agency Chief Information Officers (CIOs) must ensure software producers have implemented conformity with the following two practices:
- Obtain a Self-Attestation
- Demonstrate Conformance to Secure Software Development Practices
Let’s break these down.
Obtain a Self-Attestation
Agencies must obtain a self-attestation from the software producer before they implement that software into their operations. This self-attestation statement acts as a conformance statement, helping to prove that the third-party software is in line with NIST guidance.
If software is renewed or has major changes, a new conformance statement must be generated. If even a single practice from the NIST Guidance cannot be attested to by the software company, they must also provide a document in which they outline their mitigation, risk management, and Plan of Action & Milestones strategy to ensure the software is secure.
The memo also included the format and details of an acceptable self-attestation, which includes but is not limited to:
- The producer’s name
- A description of which products the statement covers
- A statement declaring that secure development practices have been followed
All agencies will have access to a standard self-attestation form, with the Federal Acquisition Regulatory Council attempting to create uniformity across these forms.
Demonstrate Conformance to Software Development Practices
The second action taken to ensure software integrity and reduce risk is to require all agencies to obtain a document that demonstrates conformance. The industry standard here refers to a Software Bill of Materials (SBOM). Every SBOM must follow the data formats outlined by the NTIA.
The requirement to produce a comprehensive SBOM aims to bring additional transparency to the software supply chain. Each software producer must also demonstrate that they participate in a Vulnerability Disclosure Program.
Agencies must notify all software vendors as early as possible in the acquisition process about these requirements to ensure they are fully completed.
How Will This Impact the Industry Going Forward
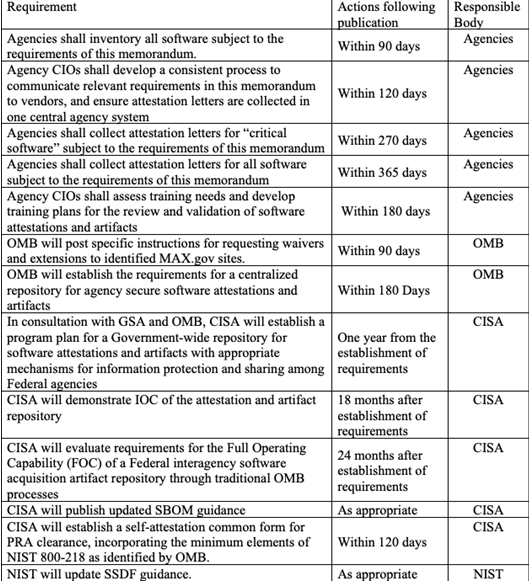
It’s important to note that these changes are not necessarily coming into action immediately. Agencies have 90 days to inventory their software, and up to 365 days to collect self-attestation letters.
https://www.whitehouse.gov/wp-content/uploads/2022/09/M-22-18.pdf
Yet, by introducing these requirements, the US government shapes the entire software supply chain. While their reach only extends to software vendors and producers supplying solutions to federal agencies, their active changes quickly become the industry standard.
We already see the popularization of SBOMs across the board, with more vendors than ever before experiencing requests for comprehensive itemized inventories. With each additional EO and memorandum, the White House pushes for a more secure supply chain. For all vendors, whether working with the US government or not, the legislated requisites will begin to passively move down the chain.
Emphasizing the importance of a secure software development environment, all vendors should begin to learn more about creating comprehensive SBOMs in anticipation of potential industry-wide impacts.
Relevant dates:
- 90 days (December 13, 2022): Agencies need to inventory all software covered by memo and flag critical software
- 120 days (January 12, 2023): Agencies need to develop a process to communicate new requirements to vendors and develop centralized system for self-attestation forms; CISA required to create a standardized self-attestation form
- 180 days (March 13, 2023): OMB to establish requirements for a centralized repository for software attestations
- 270 days (June 11, 2023): Agencies need to collect attestations for critical software
- 365 days (September 14, 2023): Agencies need to collect attestations for all software