The Software Bill of Materials (SBoM) will take center stage as the key artifact for an open source governance process in 2021. Driven in large part by a broadening array of stakeholders who need to access to its contents, we’ll see the siloed approach to building an SBoM and static way of viewing the information in it evolve to an automated, collaborative, and dynamic process.
A few underlying trends are at play here that will make managing the SBoM in Excel akin to a Fortune 100 CPG trying to catalogue all ingredients for its products in spreadsheets.
Let’s begin with the increasing complexity of open source content.
Some 80% or more of most application code in modern software comes from dependencies, code referenced and bundled to make a software package work. Dependencies can be direct or transitive, the latter being sort of dependencies of dependencies. Javascript repositories, for instance, have on average 10 direct dependencies and 683 transitive dependencies, GitHub’s 2020 State of the Octo-verse report found.
That sheer number of dependencies and increasing ecosystem (there were 60 million new repositories created in 2020 on GitHub alone) broadens the plane for risk. You simply can’t comply with and secure what you don’t know is there. And active repositories with a supported package ecosystem have a 59% chance of getting a security alert in the next 12 months.
This is all getting the attention of people who didn’t really pay very close attention to the SBoM before. There’s now a business mandate for increased visibility into the software supply chain that eclipses legal and security teams and now includes, for instance, those responsible for quality assurance, product safety and export compliance. They need visibility into the chain of custody to verify levels of encryption to ensure compliance, or better guard against vulnerabilities in the software running physical products. This is critical to preventing or fixing vulnerabilities that could malfunction and potentially cause physical harm.
The Software Bill of Materials Continues to Grow
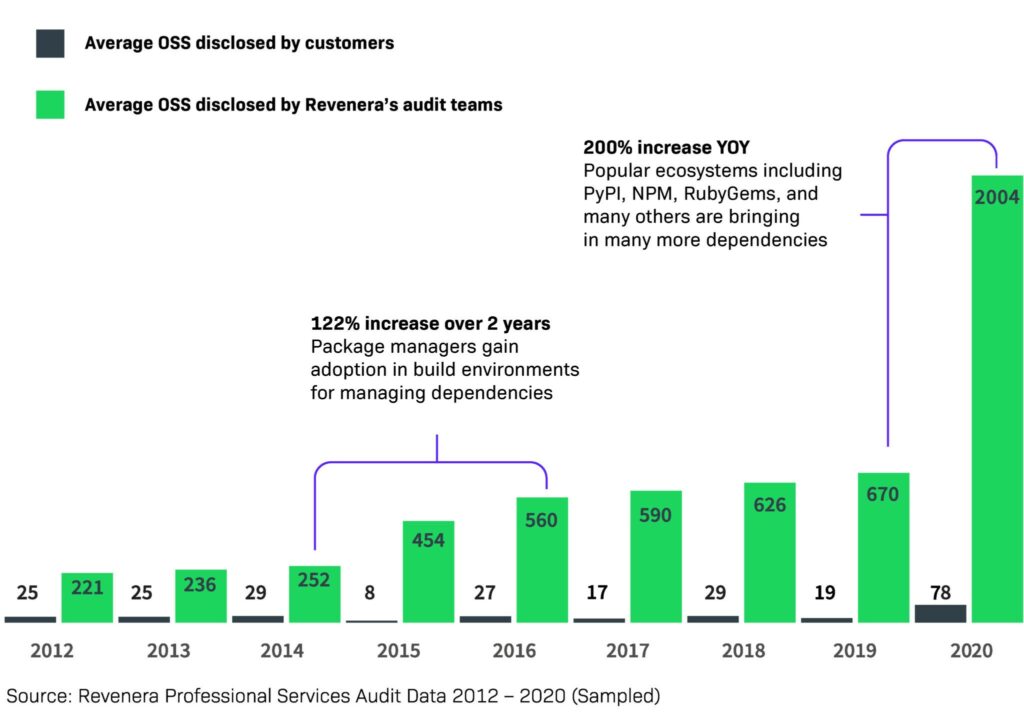 All of this is driving demand for a unified, automated approach to assembling the SBoM. People also want to view and consume accurate content in the context of their unique needs. This includes not only receiving alerts, but proactively looking for issues to answer key business questions:
All of this is driving demand for a unified, automated approach to assembling the SBoM. People also want to view and consume accurate content in the context of their unique needs. This includes not only receiving alerts, but proactively looking for issues to answer key business questions:
- What is the complete open source bill of materials for my application?
- What is the overall level of risk for my application? Where do I allocated my limited resources?
- Which items within my application are non-compliant, and where do we stand with the fixes?
- What are all the versions of a given component in use by our team? Can we consolidate?
- What are the outstanding legal and security review tasks across our portfolio of applications?
- What is the distribution of licenses across our portfolio of applications?
- Where are all my instances of Apache Struts across my portfolio of applications?
A demand for increased access, however, is meeting an ever-exploding volume of content. The result is we’re increasingly being tasked to look for needles while hay and needles continue to pile on the stack.
As an example, we’ve been collecting content since 2008.In the last 18 months, we’ve doubled our collection, meaning that in less than two years, there’s been more material put out there than in the previous 10 years combined. There’s too much out there to continue to collect and there’s too much noise in performing scans that is leading to false positives – the detection of issues that don’t actually present valuable results. To reduce noise and enable more proactive threat and risk detection, in 2021 we’ll see enhanced functionality and more efficient approaches to OSS governance with the SBoM when it comes to what we collect and how we scan. Software Composition Analysis (SCA) technology that enables real-time lookups and provides the capability for ad-hoc queries will help streamline the process while still ensuring accuracy. Not everything on GitHub gets released. Many repositories are school projects or internal test builds. There’s not a need to collect everything anymore. Advanced filtering capabilities will become critical to ensure that important content is being cataloged while leaving the superfluous repositories behind. Organizations will also look for advanced filtering capabilities, both top-down and bottom-up, which prioritize exceptions and allow for setting thresholds informed by past use and correlation to other results. This will enable teams to focus on what is relevant in the context of the task they’re trying to perform, because depending on what open source you’re using and how the organization is using it, you may not have to look at every line of code. Managing by exception and within your level of risk tolerance will dictate the depths to which your organization will go.
2021 will be the year in which comprehensive SCA solutions are used in a continuous and automated manner to drive governance programs based on established industry best practices – coupled with a realization of the value that a complete and accurate SBoM presents across the business. Read about all of the Top 10 Trends in Open Source Software Compliance or listen to the full webinar here.



