SOFTWARE MONETIZATION PRODUCTS
Software License Compliance - Compliance Intelligence
Compliance Analytics to Detect, Identify and Convert Unpaid Software Use
Revenera Compliance Intelligence
Generate New License Revenue from Software Piracy and Overuse
Globally, 37% of users are not paying for software making it a $46.3B problem. But eighty-three percent of these unlicensed users in mature markets are legally-inclined victims of software piracy who will pay for software. Compliance Intelligence (formerly Revulytics) helps software suppliers systematically monetize the unpaid use of their applications. When software suppliers detect and identify this unpaid use, they can act on this forensic evidence to power their compliance and revenue generation strategies.
Compliance Intelligence detects, identifies, and reports on organizations using your software without paying for it. Infringements are transformed into actionable leads for your sales and compliance team through our proprietary federated database system. Leads are delivered right to your existing CRM or a force.com instance and flexible controls provide role-based access to authorized internal and external users.
Converting unpaid users is an untapped revenue stream. Our customers - from the largest EDA, PLM, and engineering software providers, to smaller prosumer software vendors - have generated $4.2 billion in new license revenue since 2010 using this approach.
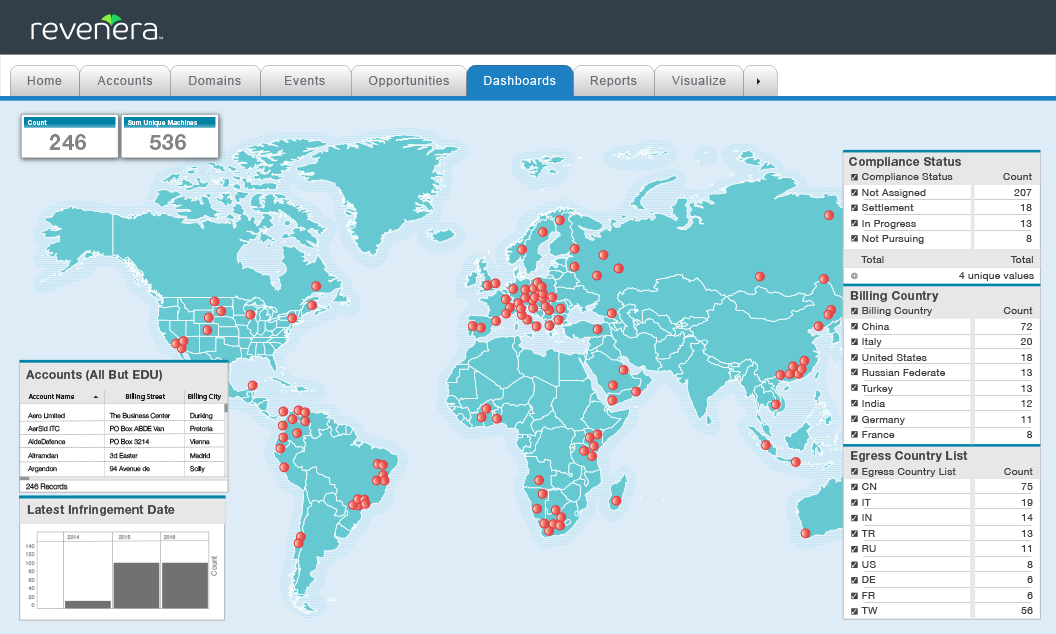
Compliance Intelligence (formerly Revulytics) detects and identifies global software license compliance infringements.
WHAT IT CAN DO
Monetize the Misuse of Your Software:
- Generate new license revenue
- Identify unpaid use with confidence
- Uncover and validate infringer identities
- Enhance data with wi-fi geolocation
- Make data you’re already collecting more actionable
Act on Verfied Misuse of Your Software:
- Uncover infringers globally, from software pirates to license overuse and misuse
- Infringement data is transformed into fully resolved organizational identities to accelerate qualification for sales and compliance
- Improve the data you’re already collecting on infringing organizations such as activation, licensing entitlement, and other telemetry data. Leverage enterprise-class technology including Force.com and Tableau, integrated with your CRM, licensing, and BI processes to drive operational efficiency. Reach out and convert leads with your internal teams, or leverage our revenue services for assistance in converting pirates in countries where you may not currently have a local presence
We’re achieving all the things we set out to do. We’re realizing revenue, we’re reducing our piracy problem, and at the same time we’re maintaining strong customer relationships. We’ve never had to take legal action, and as often as not, we get a thank you for ‘bringing this information to our attention and giving us the opportunity to resolve it.
Data-Driven License Revenue
See how Compliance Intelligence enables you to convert unlicensed users to paying customers.
SOLUTION OVERVIEW
Data Optimization
- Accelerate identification of infringers
- Qualify compliance leads with confidence
- Prioritize your best revenue opportunities
- Partner with dedicated data experts
Data Enrichment
- Bring your own telemetry data
- Better identify and validate infringing use
- View a centralized platform for visibility and control
In-application Messaging
- Reach and educate unpaid users
- Target conversion offers
- Optimize ecommerce campaigns
- Drive conversion by changing application behavior
Resources
Data Sheet
Compliance Intelligence
Compliance Intelligence provides software vendors with actionable intelligence on the unpaid use of their applications to generate new license revenue.
Industry Report
Forrester Total Economic Impact Study
Learn More About 426% ROI and Operational Efficiencies Enabled by Revenera
Report
Software Piracy and Compliance 2025 Outlook
This report in our Monetization Monitor series for the latest trends in software piracy, overuse, and misuse. Discover how data-driven insights can help prevent future losses.
Webinar
Generating Revenue and Growing Customers from Software Piracy
Join John Hollows, Senior License Compliance Operations Manager at Bentley Systems, and Revenera’s Victor DeMarines and Erin Barrett, as they discuss how to take a data-driven approach to software piracy and more in this Revenera webinar
Online Event
Building Software License Compliance Programs in a Cloud World
Join Revenera VP, Product Management, Software Monetization, Vic DeMarines for a discussion that will dispel myths and assumptions about what it means to run a software compliance program in 2023 and beyond.
Case Study
Ramping Up a Profitable New Compliance Program
Developer of engineering tools driving new revenue throughout North America and Europe with Revenera.
From the Blog
Blog
How to Accelerate Your Quote-to-Cash Process
Blog
How to Launch Usage-Based Pricing for SaaS and AI
Blog
Your Ultimate Guide to SaaS Pricing Models
Want to learn more?
See how you can generate new license revenue from software piracy and overuse.