SOFTWARE COMPOSITION ANALYSIS
Mitigate Risk in Your Software Supply Chain
End-to-end solution to deliver a complete, accurate SBOM while managing license compliance and security
Create Trust in Development
Developers are leveraging more and more open source software (OSS) in their software applications. As a result, the Software Bill of Material (SBOM) is getter larger, more complex, and more difficult to secure.
Software Composition Analysis (SCA) solutions from Revenera help you discover, assess, and manage license and security risk across all your software applications.
Our mission is to support the construction of a complete and accurate SBOM to manage Legal and Security risk, and deliver compliance artifacts required by your compliance programs.
Revenera achieves OpenChain 2.1 Conformance for license compliance
Why Revenera
Code Insight from Revenera provides the most complete, accurate SBOM in the industry. We don’t just stop at software packages, containers, and dependencies. Code Insight allows organizations to go deeper.
WITH SCA FROM REVENERA
Manage a complete SBOM in a SaaS environment
- Ingest SBOM data from a wide range of sources
- Unify internal and external SBOMs across your organization into a single actionable view
Discover and track all open source, third-party, and commercial software
- Manage open source license compliance and reduce IP risk
- Identify and fix open source vulnerabilities
- Run flexible scans based on situation and need
CHECK THE NUMBERS
60%
of organizations building or procuring critical infrastructure software will mandate an SBOM by the year 2025
86%
of developers said they sometimes or always try to find open source options over other kinds of software
81%
of organizations are moderately to highly concerned about risks surrounding suppliers and partners.
<10%
How much open source usage organizations are aware of
61M
new OSS repositories were created on GitHub last year
95%
of organizations are concerned about software security.
We just couldn’t operate now without the ability to automate code scans using Software Composition Analysis. Our use of Code Insight is only going to grow as we bring on more developers, develop more applications, and substantially grow our business.
Never Miss Parts in Your SBOM
From full software packages to code snippets to delivering the most complete, accurate SBOM, Revenera’s software composition analysis solutions scan your source code, binaries and dependencies for software vulnerabilities and license compliance issues. We integrate with common build tools and provide one of the largest open source knowledge bases in the industry, with more than 18 million components.
Ingest SBOM data from sources outside your organization, unify all the data—both internal and external—and publish a complete, accurate SBOM to your customers and downstream partners.
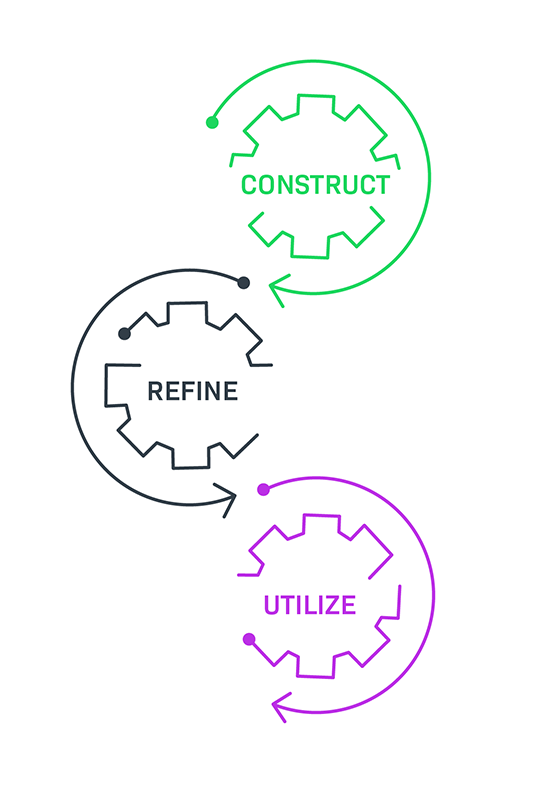
CONSTRUCT
Your SBOMs representing your portfolio of applications consist of parts that come from many different places, both inside and out of your organization. This phase takes all that SBOM data – including open source components, third-party code, and commercial – reconciles it, and presents it in an actionable unified view.
REFINE
Because the data is coming from multiple sources, there are varying levels of quality. There may be gaps to fill, issues to resolve, and needed adjustments to further refine your SBOMs before publishing them for internal or external consumption.
UTILIZE
Now that your SBOM source of truth is catalogued, fulfill obligations and assess your security and compliance risk with confidence. Generate compliance artifacts, view usage insights and trends, and perform impact analysis – as new vulnerabilities are discovered – to allow your development, security, and legal teams make better decisions for your business.
Revenera SCA
SBOM Management
SBOM Insights gives organizations the ability to manage security and legal risk by maintaining a complete and accurate SBOM in the cloud. Expand your level of transparency into your products beyond the code under your control by aggregating the SBOM over multiple data sources.


Scan and Analysis
Code Insight is a single integrated solution for open source license compliance and security. Find vulnerabilities and compliance issues and remediate risk.
Audit Services
Revenera's team of auditors have examined tens of thousands of software projects in the past 15 years while helping customers understand the composition of their source code.

BUSINESS SOLUTIONS
Resources
Webinar
The Supply Chain Risk You Can’t Ignore: A Playbook for Critical Industries
Thursday, June 26, 2025
The webinar will benefit development leads, CIOs, and CTOs responsible for navigating compliance and mitigating supply chain risks. Don’t miss out to gain actionable insights for protecting your organization in an increasingly complex environment
Online Event
User Group 2025 - Software Composition Analysis
Thursday, September 25, 2025
Register for Revenera’s Software Composition Analysis User Group 2025. The annual customer event that will provide the latest industry trends, case studies and product developments.
White Paper
Risky OSS: How Regulated Industries Can Secure the Software Supply Chain
This whitepaper reviews the state of OSS, four management use cases, and best practices and solutions to help security and legal teams in highly regulated industries. Access now to learn how you can confidently mitigate rising supply chain risk.
Data Sheet
OSS Inspector Plugin
Ensure your code is secure and compliant by effortlessly managing open source dependencies directly in your IDE.
Webinar
The Beginner’s Guide to Managing Open Source Software
Join this beginner’s guide to OSS, SCA, OSPOs, and SBOMs to get started on your open source journey. In this productive webinar session by Revenera’s open source expert, Alex Rybak.
Webinar
Setting up your OSS Management process
Join our expert team as they walk you through how to setup a comprehensive OSS Management program to address both software supply chain security and legal compliance, in this live webinar.
From the Blog
Blog
Development Security Best Practices: Our Top 5 Suggestions
Blog
Likely Exploited Vulnerabilities (LEV): Breaking Down the New Metric from NIST
Blog
The EUVD is Here: What it Means for the Future of Cybersecurity
Want to learn more?
See how Revenera's end-to-end solution delivers a complete, accurate SBOM while managing license compliance and security.
